

Hararei is a Value–Added Reseller for leading edge technologies in the security, cloud and data protection domains. We have the skills to integrate Internet Security, Cloud Hosting, SDWAN, and Data Protection solutions into your environment.
The Secure Application Services Edge (SASE) is the most important development is infrastructure architecture occuring right now. When first defined by Gartner in 2016, the architecture was aspirational, but is now becoming the most important way to deliver applications to users and consumers.
Zscaler Internet Access (ZIA) is the world’s leading Secure Web Gateway (SWG), delivering cloud–native, AI–powered cyberthreat protection and Zero Trust Network Access (ZTNA) to the Internet and SaaS apps. Zscaler’s proxy architecture enables full TLS/SSL inspection at scale, with connections brokered between users and applications based on identity, context, and business policies. ZIA is part of the Zero Trust Exchange (ZTE), and all Internet–bound traffic is be sent through the ZTE.
Zscaler Internet Access (ZIA) Sits inline between your company and the Internet, protecting your enterprise from cyberthreats, stopping intellectual property leaks, and ensuring compliance with corporate content and access policies.
ZIA monitors your network and user activity, secures roaming users and mobile devices, and manages all of this globally from a single management console. There is no hardware to buy, no appliances to manage and policy changes can be effected globally across your organization from a single console in minutes.
Zscaler Internet Access (ZIA) can protect your employees from malware (including Ransomware), viruses and other Internet threats, blocking attacks in real time. Zscaler security services scan and filter every byte of your network traffic, including SSL-encrypted sessions , as it passes to and from the Internet.
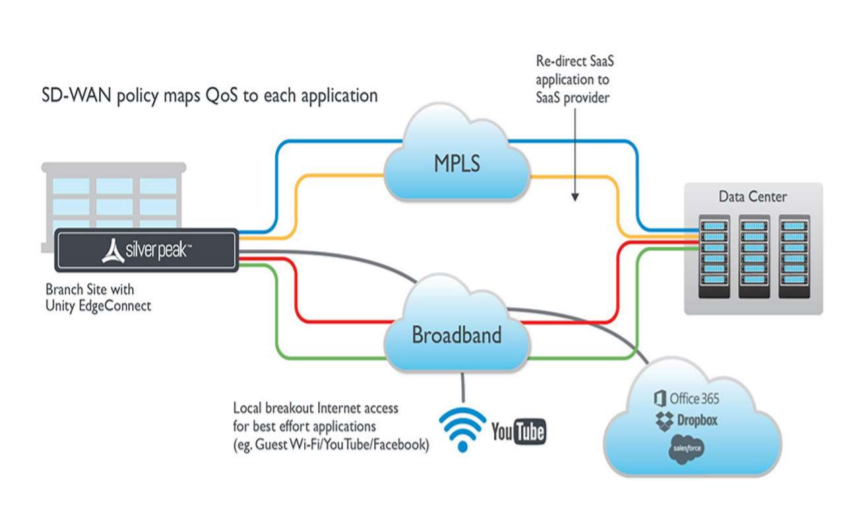
Zscaler Internet Access (ZIA) provides a Secure Service Edge (SSE), which when combined with an SD–WAN product such as Aruba EdgeConnect can provide a complete SASE architecture. It allows secure local breakout for your branch network. SD–WAN makes local breakouts easy. Zscaler makes them secure. Learn more: Network Transformation
One advantage of a cloud–delivered security gateway is that it can be delivered very quickly. See Rapid Internet Protection for a discussion on how protection can be enabled very rapidly. One major airline in the United States, responding to an urgent cyber–event deployed Zscaler to the majority of its users (over 60,000 users) over one weekend, and that included planning time!
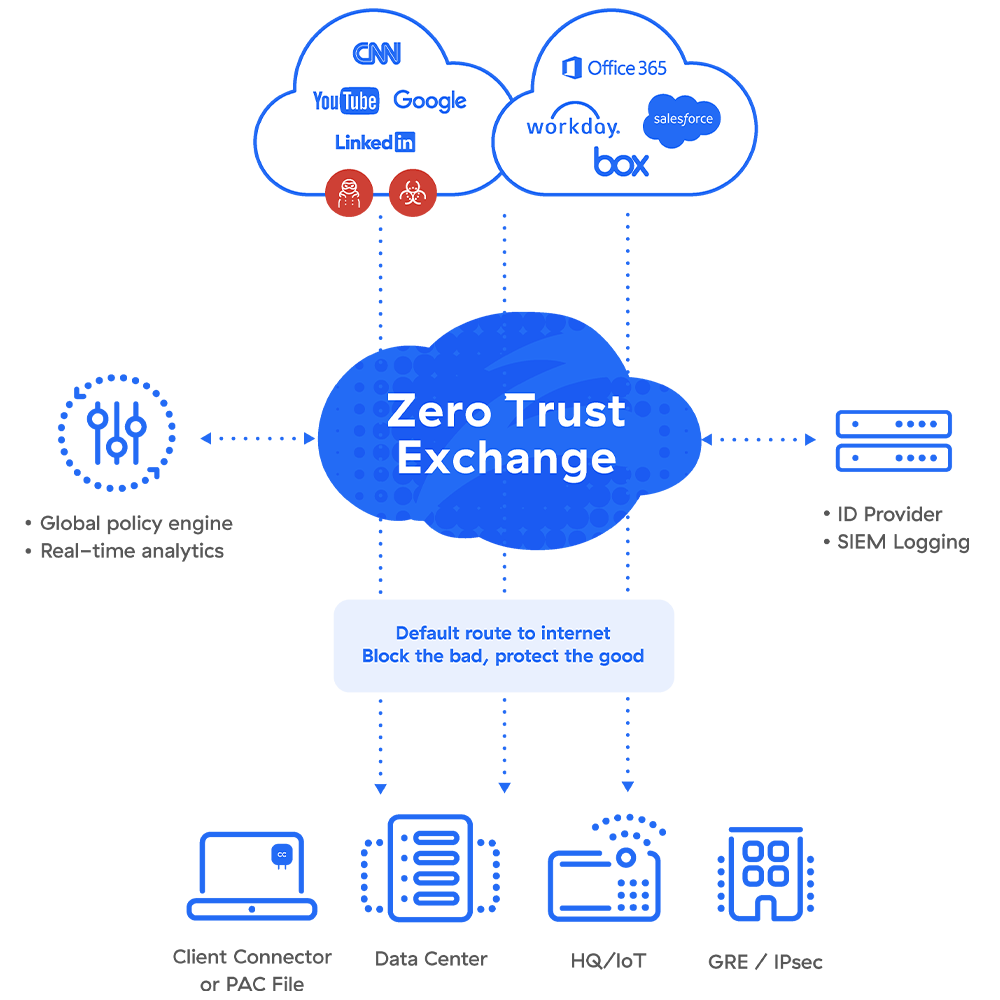
The Zero Trust Exchange (ZTE) is the core component of the Zscaler Secure Web Gateway. All traffic, including encrypted traffic can be routed through the ZTE for inspection and control
Not sure if your current Internet secure web gateway is really secure? Conduct a Security Preview now, from within your existing network to show how effective your current controls are.
The Zscaler Security Preview runs in your
browser. It does not access any data, introduce malware or change any
settings. Click on the adjacent image to begin the Security Preview
Zscaler can also help protect IoT (Internet of Things) and OT (Operational Technology) environments, and help to enable Industry 4.0 in industrial environments. Zscaler can allow for secure data exchange in IoT environments such as Smart City and power generation, and help protect legacy OT environments by providing a Zero Trust Exchange between OT and IT systems.
ZTNA, or Zero Trust Network Access, provides secure, identity-based access to private applications and data for users and devices by verifying their identity and device health before granting temporary, granular access to only the necessary resources, rather than broad network access. It replaces traditional VPNs by creating a "software-defined perimeter" (SDP) for each user and application, significantly reducing the attack surface and improving security for modern, cloud-first organizations.
Zscaler Private Access (ZPA) is a next-generation, non-VPN based solution for secure remote access. The patented Zscaler Private Access solution works by abstracting the private, internal application from the network on which it resides, providing access from authorized users to specific applications via encrypted, per–session microtunnels that are created upon demand.
The end user is never directly connected to the application, nor is the user connected to the network on which the application resides. ZPA instead delivers functionality similar to a forward and a reverse proxy acting together. This ensure that networks and applications cannot be infected or exploited by open network tunnels.
Zscaler is a platform, which means Zero Trust can be combined with other security functions such as Data Loss Prevention, Cloud Application Access, Application Bandwidth Management, and Secure Web Gateway in a single platform. This platform can then be used for management and complicance reporting and security monitoring. For an example of a holistic platform approach to application, see our Zscaler for SAP page.
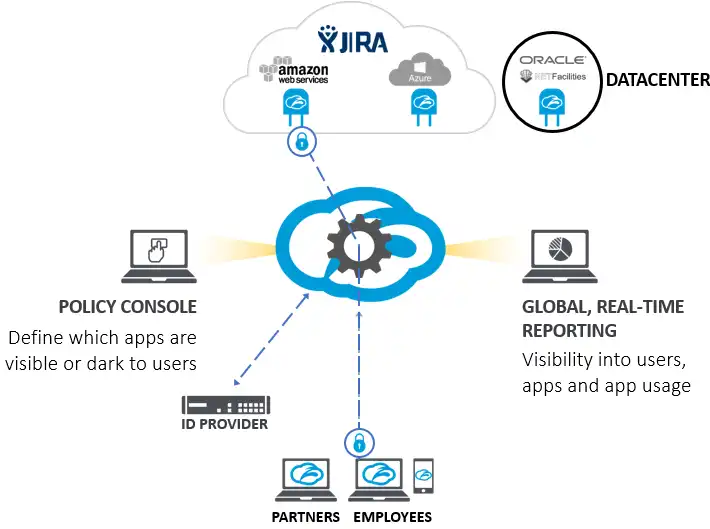
Zero Trust Network Access is one component of a Secure Access Service Edge (SASE) architecture.
Learn more at: Zero Trust Network Access
Enforce Zero Trust in branch offices with a built–in next–generation firewall providing IDS/IPS and ole–based segmentation capabilities. Replace legacy branch firewalls and reduce hardware footprint.
Simplify and automate secure multi–cloud connectivity to leading Cloud and SaaS providers, extending the benefits of SD–WAN and delivering the highest levels of application performance.
Because not all SD–WANs are created equal, build a modern WAN that assures the highest performance and availability, whether applications reside in the data center or the Cloud
Understand the business value and financial impact of SD–WAN through a customer value assessment, analyzing traditional network challenges and justifying a shift to SD–WAN
Aruba’s EdgeConnect provides secure and reliable virtual network overlays to connect users to applications with the flexibility to use any combination of transport technologies without compromising security or performance.
Aruba EdgeConnect enables customers to use broadband connections to augment or replace their current expensive MPLS networks, and to optimize site-to-site VPN traffic.
Predictable application performance and availability over any combination of transports:
Silver Peak’s SD-WAN solution improves the user experience, increases
application performance, and significantly reduces capital and
operational expenses by up to 90%.
Secure, Encrypted SD-WAN: With increased snooping on networks, insecure default hardware configurations, and an uncertain chain of custody for international networks, what can an enterprise do to ensure their private data stays private? Learn how Hararei can help to secure your WAN traffic: Secure Overlay Network.
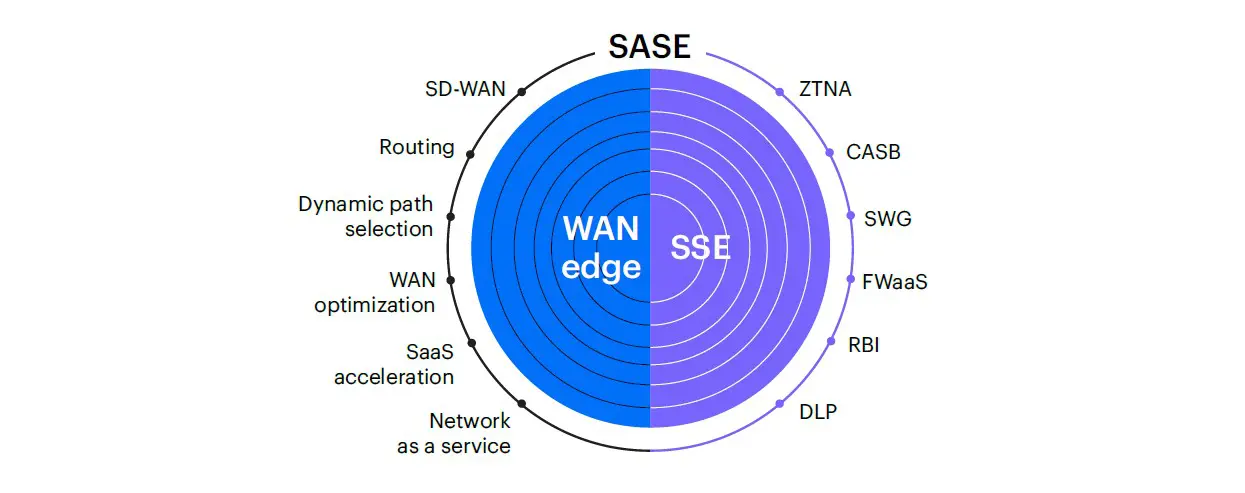
Expanding use of Cloud applications, relentless cyber attacks, increased bandwidth requirements, mobile workforces and the growth of newer technologies like IoT all add up to greater security challenges facing organizations. Secure Access Service Edge (SASE) architectures address the need for improved agility and performance, and increased network security.
What Is SASE?
SASE is the combination of an advanced SDWAN edge deployed at the branch and comprehensive cloud–delivered Security Service Edge (SSE)
By transforming both WAN and security architectures with SASE, enterprises can help ensure direct, secure access to applications and services across on–premise and multi–cloud environments, regardless of the users and devices used to access them.
At Hararei, we recognize that it is a journey for any mature organization to adopt a new infrastructure architecture, and can help guide your adoption of these Cloud Generation technologies

Single–vendor SASE offers organizations the many benefits of SASE, while making adoption simpler and more cost–effective. Look for a solution that is integrated, unified, flexible, and easy to use
SASE adoption is rising and deployment preferences are mixed. Research conducted by Ponemon Institute shows nearly two–thirds of organizations have deployed, or plan to deploy SASE in 2025. At Hararei, we have been deploying and managin SASE for our customers for over 8 years
The Cloud service model has evolved to the point where IT and business leaders usually ask why applications cannot be delivered on the Cloud. Whether the model is public or private, IaaS, PaaS or SaaS, it is usually cloud first
More and more companies are embracing the Public Cloud for IaaS/PaaS.
Cloud migrations can range from simple provisioning of a couple of AWS virtual servers, to entire applications with stringent data protection requirements, or to entire enterprises with complicated global privacy and regulatory requirements. Consider the following solutions for your Cloud Journey:
Leveraging AWS best practices, Hararei partners with you to define a multi–phased roadmap for your Cloud Journey:

Hey IT, don't fight it! Embrace it! Adopt a Cloud First strategy to support your business’s digital transformation.
Remember, at the end of the day, every CEO (yes, EVERY CEO!!!) only cares about three things:
IT started to embrace public SaaS years ago (SalesForce.com, WebEx, HR/Payroll services, etc.). And now, more and more companies are leveraging IaaS and PaaS in the public cloud too. Why? Simple - their IT leaders realized that the benefits associated with public cloud (time to market, speed, agility, no CapEx, low OpEx, feature rich, flexibility, scalability, elasticity, security, etc.) will help to achieve some if not all of things CEO's care about.
Hararei provides a range of cloud-based Disaster Recovery solutions to suit every budget and recovery objective. From simple Backup/Restore solutions to full-scale Active/Active solutions that operate across multiple sites or Clouds, Hararei can help you implement a Disaster Recovery solution that meets your requirements.
Hararei is an AWS Consulting Partner and has the commercial IT experience to properly architect and implement a robust Disaster Recovery strategy
Many companies provide a Disaster Recovery environment to ensure continued operation during natural disasters, political strife, epidemics or other potential disruptions to business. The IT Disaster Recovery Plan is typically part of a wider Business Continuity Programme, and it can be a major expense for any company.
Expenses involved in providing a Disaster Recovery capability can often approach (or even exceed, due to data replication requirements) the cost of the primary IT Production costs, which leads some comapnies to try to save money by reducing the capabilities in the Disaster Recovery environment.

The good news is that Amazon Web Services (AWS) can be used as part of a strategic IT Disaster Recovery Plan and will usually be lower in cost than existing capabilities, and most likely provide a better time to recovery. We outline 4 different strategies here that can form the basis of an effecient and cost-effective Disaster Recovery plan:
The actual strategies used depends on RTO/RPO requirements and budgets, and will be different for every company
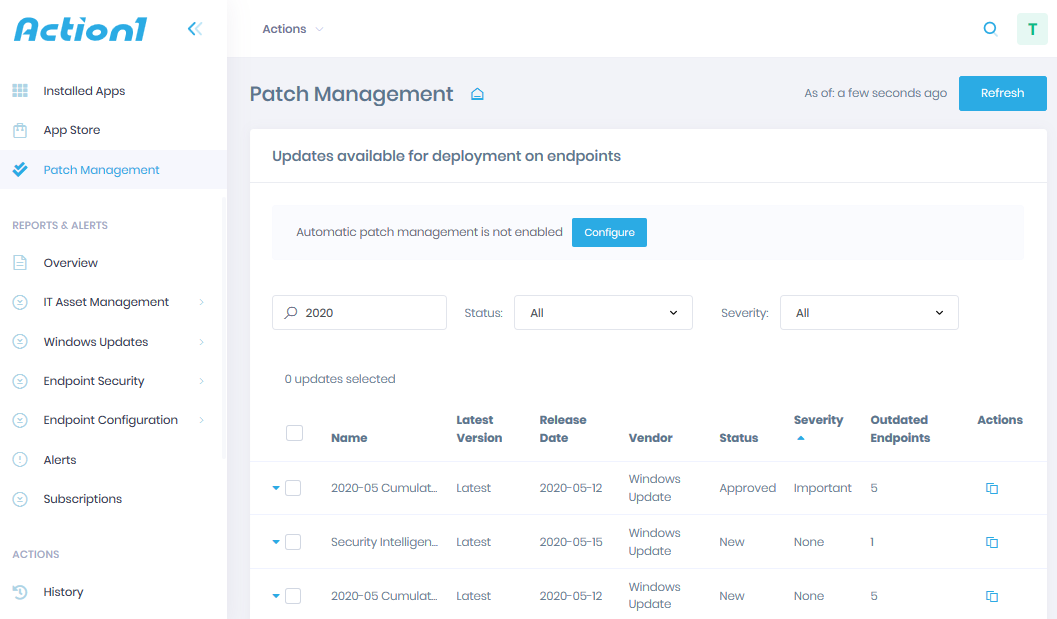
Patch management is the process of remediating software vulnerabilities by sourcing, distributing and applying software updates and is the most important part of a vulnerability management program.
Patching helps to fix security vulnerabilities in operating systems and applications before they are exploited by threat actors. Operating System and Application patching is a vital layer of defense against malware and ransomware attacks.
Action1 is a highly rated, easy to use SaaS application that helps manage patching across a range of endpoints, and is suitable for enterprises large and small.
MSP360 provides software for backups to the Cloud with limitless point in time restore capabilities, ensuring that even if you are hit with a ransomware attack, you can roll back your user devices to a point prior to the attack
MSP360™ (formerly CloudBerry Lab) is an easy-to-use cloud backup management solution with military-grade encryption.
Customers can choose to provision their own storage using any of the major cloud storage providers including AWS, Microsoft Azure, Google Cloud, Wasabi and others, or Hararei as an AWS Partner can provide AWS storage. Unlike other solutions, the customer is NOT locked into a storage provider.
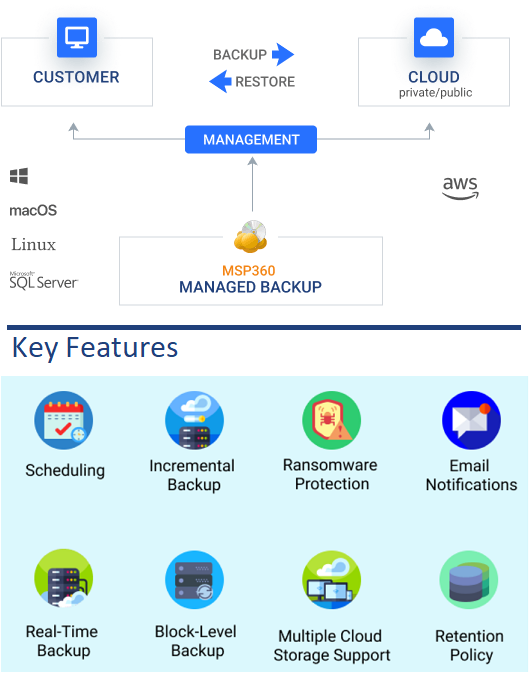
Key features include:
Security Management remains a critical function for IT departments regardless of where applications are hosted or what the connectivity looks like. Protecting the organization from endpoint to data center requires a holistic approach that crosses multiple technical domains.
Prevention is better than a cure.
Arctic Wolf Aurora Endpoint Defense is a next generation end-point security solution for desktops and servers.
Aurora provides continuous threat prevention powered by Artificial Intelligence (AI).
Unlike traditional anti-virus products that rely on signatures to
detect
threats in the environment, Arctic Wolf Aurora Endpoint
Defense:
Aurora's EPP and EDR capabilities are unmatched and provide a Predictive Advantage of over 24 months (i.e., an end-user would have been protected even if they hadn’t updated their AI math model for over two years). Learn more
Protection against ransomware requires a multi-layered approach, with both preventative measures and recoverability capabilities. Learn how Hararei can provide complete protection at Ransomware Protection.
With unmatched effectiveness, minimal system impact, and zero-day prevention, Arctic Wolf Aurora protects endpoints and organizations from compromise.
Advanced threat monitoring, analytics, and expert human oversight to identify, investigate, and neutralize cyber threats around the clock.
The Managed Detection and Response (MDR) market is expanding rapidly as organizations seek smarter, faster ways to defend against an ever–evolving cyber threat landscape. With attacks growing in sophistication and an ever–increase shortage of skilled analysts, MDR has become the preferred approach for achieving continuous monitoring, proactive threat hunting, and rapid incident response.
Arctic Wolf’s MDR delivers round-the-clock monitoring, detection, and response across endpoints, networks, and cloud workloads. Leveraging advanced analytics and machine learning, the service surfaces and prioritizes threats in real time while a dedicated Concierge Security® Team works with your organization to guide containment, remediation, and long-term posture improvement. The result is a true security partnership that boosts visibility, accelerates response, and strengthens resilience against today’s rapidly evolving attacks.
HPE Aruba Networking ClearPass Policy Manager provides role and device–based secure network access control for Internet of Things (IoT), BYOD, corporate devices, as well as employees, contractors, and guests across any multivendor wired, wireless and VPN infrastructure.
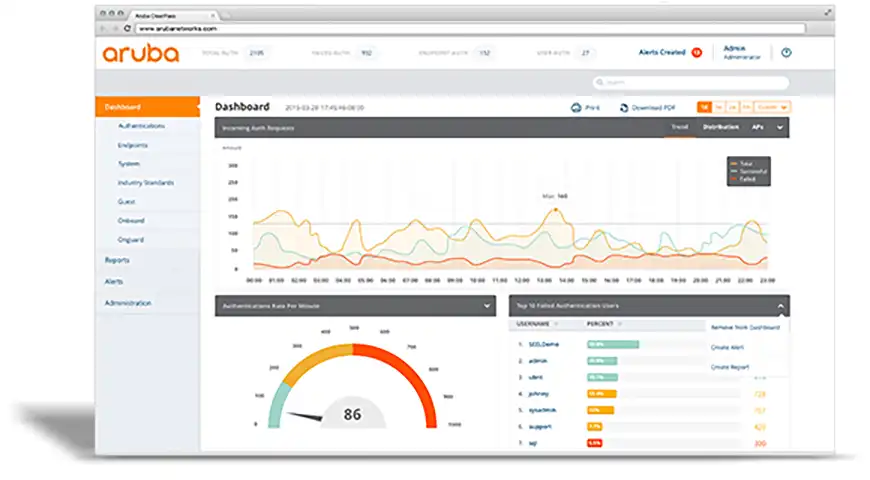
Aruba ClearPass gives you comprehensive and precise profiling, authentication and authorization for your users and guests, your systems, and devices trying to access your IT resources. It’s a rock–solid, affordable solution to control access to your network
With a built-in context-based policy engine, RADIUS, TACACS+, non-RADIUS enforcement using OnConnect, device profiling, posture assessment, onboarding, and guest access options, ClearPass is unrivaled as a foundation for network security for organizations of any size.
With ClearPass, organizations can deploy wired or wireless using standards-based 802.1X enforcement for secure authentication. ClearPass also supports MAC address authentication for IoT and headless devices that may lack support for 802.1X. For wired environments where RADIUS based authentication cannot be deployed, OnConnect, offers an alternative using SNMP based enforcement.
HPE Aruba Networking ClearPass is the only policy platform that centrally enforces all aspects of enterprise-grade access security for any industry. Granular policy enforcement is based on a user’s role, device type and role, authentication method, UEM attributes, device health, traffic patterns, location, and time of day.
Contact Us Please contact Hararei for an in-depth discussion on using any of our Cloud or Cybersecurity products or services