

ZTNA, or Zero Trust Network Access, provides secure, identity-based access to private applications and data for users and devices by verifying their identity and device health before granting temporary, granular access to only the necessary resources, rather than broad network access. It replaces traditional VPNs by creating a "software-defined perimeter" (SDP) for each user and application, significantly reducing the attack surface and improving security for modern, cloud-first organizations.
As companies ask their employees to work from home during periods of crisis, they are finding that the hardware–based legacy VPN is unable to cope with the demand. This causes their employees to be unproductive, as they cannot access critical systems and files stored on the company network.
In all liklihood the remote access solution deployed by a company was sized to handle a small number of essential personnel who need to occasionally work from home. With companies asking all (or a major proportion) of their employees to work remotely, the existing infrastructure cannot keep up. Ordering extra hardware may takes weeks.
As companies turn to their hardware suppliers for VPN appliances, they may also find that supply chain issues mean the legacy solution cannot even be purchased or deployed
The Zscaler Private Access (ZPA) solution does not use any hardware, and is entirely cloud–driven and can be delivered with the speed of a software deployment.
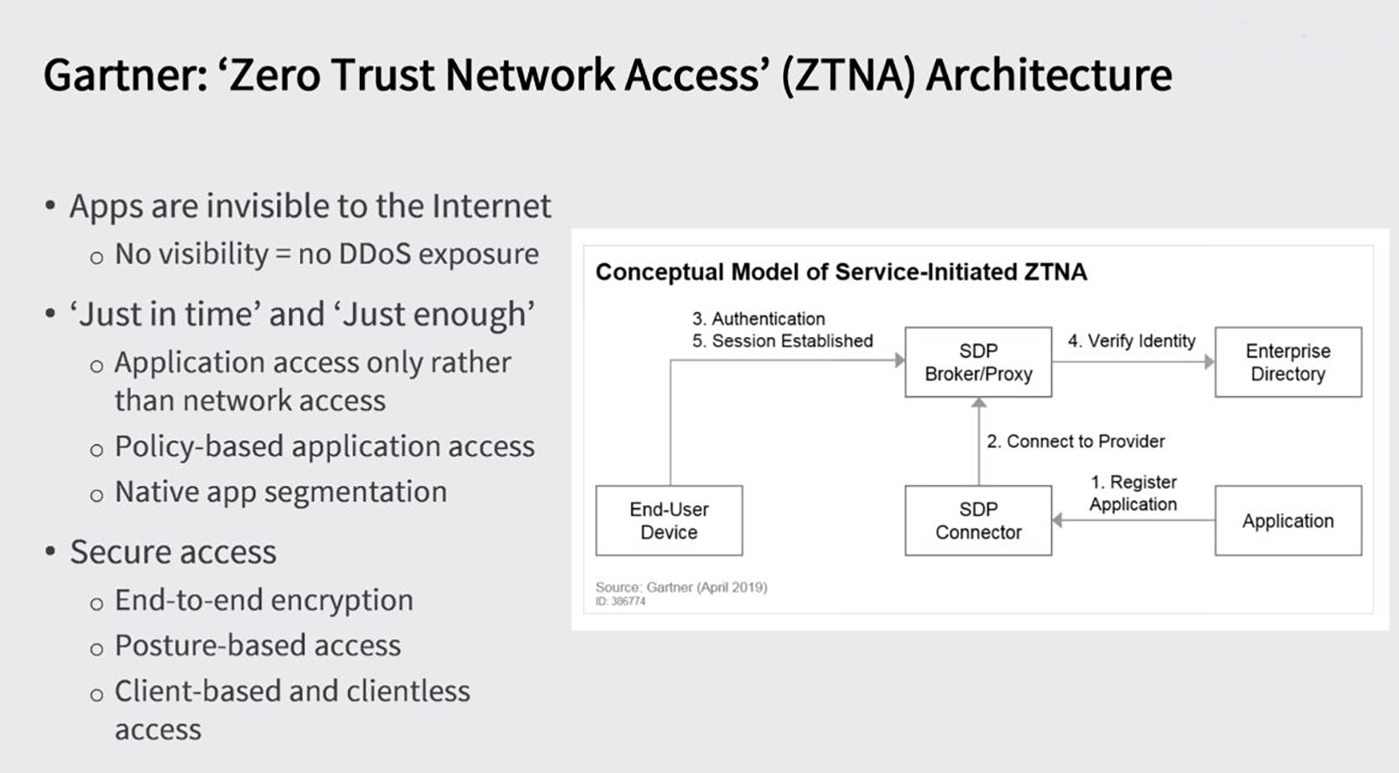
Gartner ZTNA Architecture
Legacy, hardware–based VPNs are not scalable to the demands being made of them when a significant proportion of the workforce is being asked to work from home.
ZPA allows enterprises to break free from the pain that their VPN has caused for years and move to a cloud–first approach — fundamentally decoupling security from the Data Center and moving enterprise security to the scalability, velocity and reliability of the Cloud.
ZPA delivers a secure remote access solution that can be deployed anywhere globally in a matter of minutes or hours, is more secure than traditional VPN, requires no hardware and is easier for users to use.
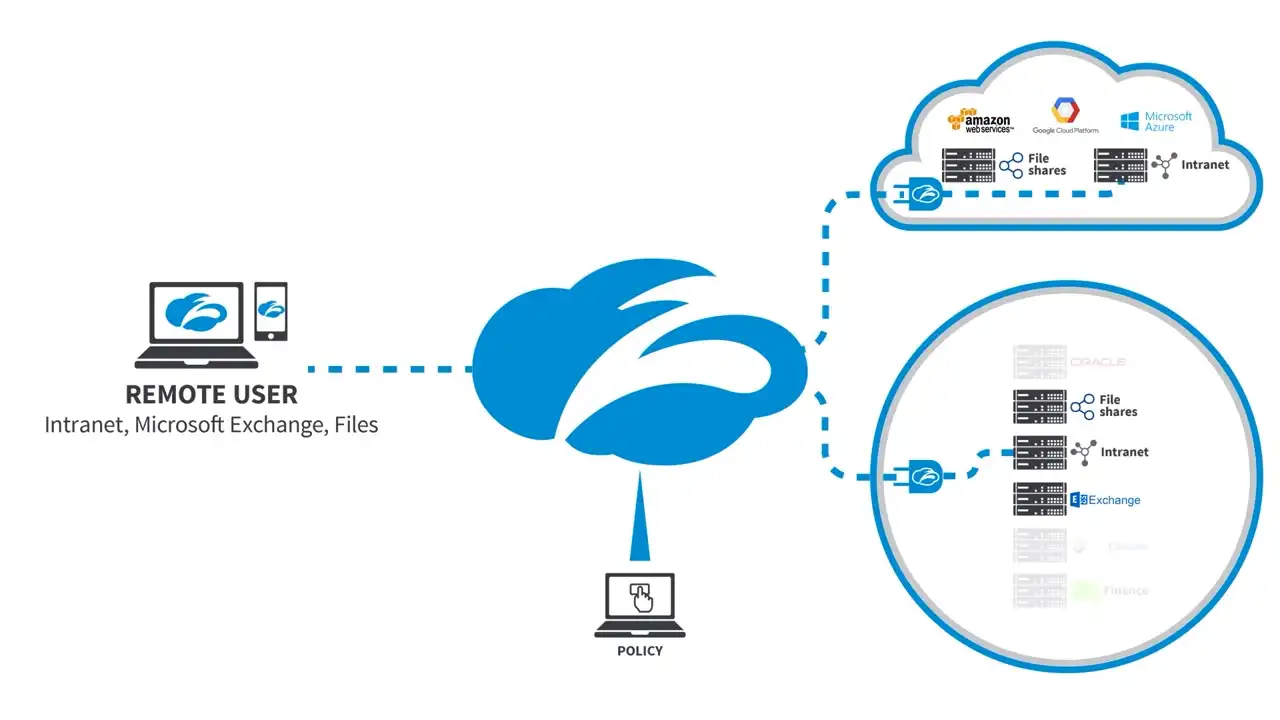
ZPA Architecture
The Z–Connector provides application load balancing across application servers and monitors application usage — anomaly detection
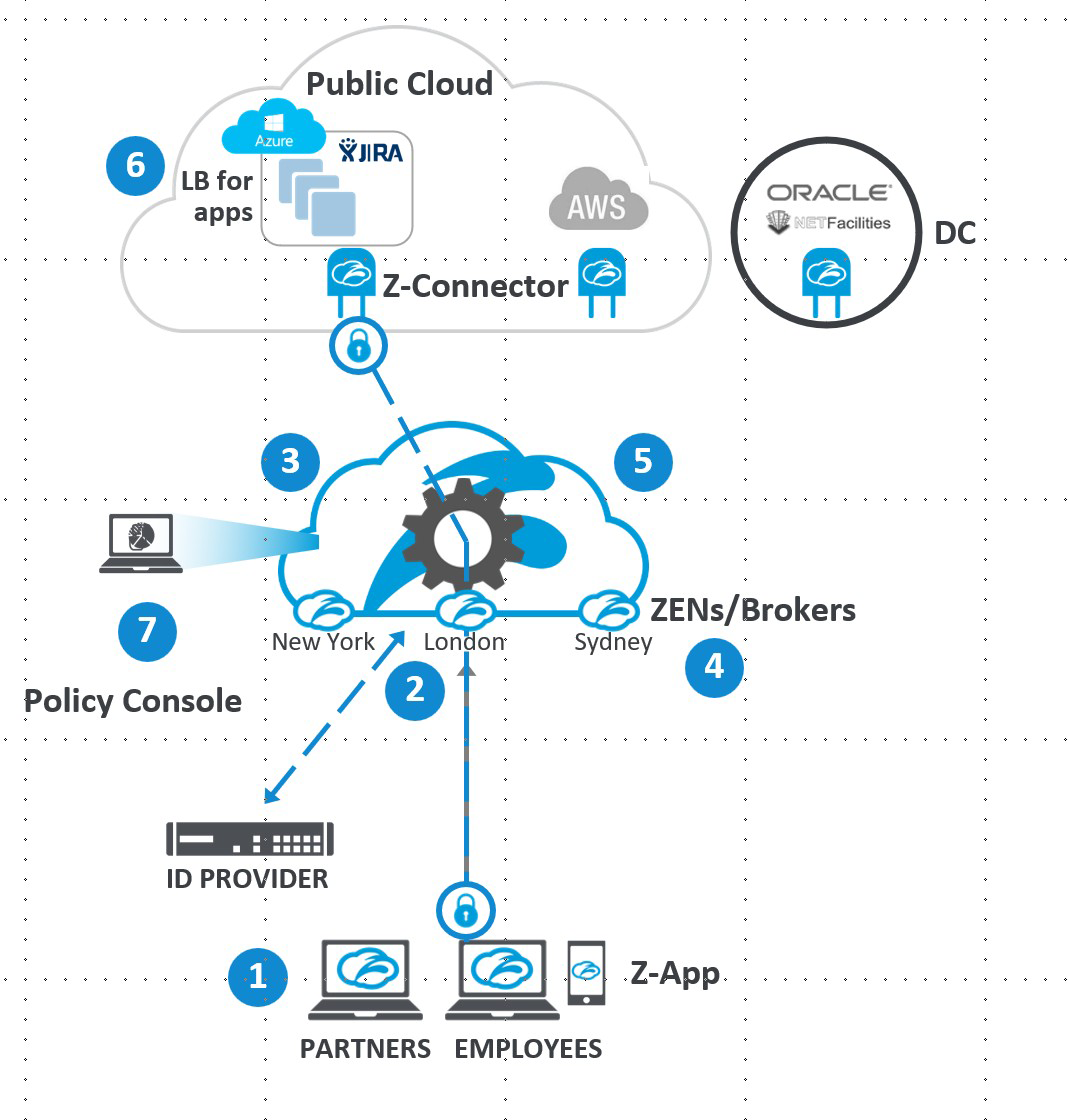
How ZPA Works
You can access free technical videos for ZPA here: Detailed ZPA Technical Training
Contact Us Please contact Hararei for an in-depth discussion on using any of our Cloud or Cybersecurity products or services