
The deadline for federal contractors to comply with DFARS clause 252.204–7012 (Safeguarding covered defense information and cyber incident reporting) is drawing near. Small and large companies alike who do business with the Department of Defense and wish to continue doing business with the agency are required to implement NIST SP 800–171 standards, as soon as practical, but not later than December 31, 2017. NIST SP 800–171 is a directive for Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations. This clause flows down to all subcontractors and teammates so any vendor that does business with the federal agency directly or through their primes must demonstrate compliance with the requirements.
While the NIST SP 800–171 regulatory requirements are laced with lots of technical jargon and terms that may be foreign, you will be surprised to find that a lot of it can be boiled down to common sense and basic IT security measures that are necessary to protect your systems and data. Amid the rise of cyberattacks, many of the requirements force businesses to practice good security hygiene which ultimately benefits companies. Adopting good security practices will not only enable your business to comply with the regulations but it will also protect your valuable digital assets.
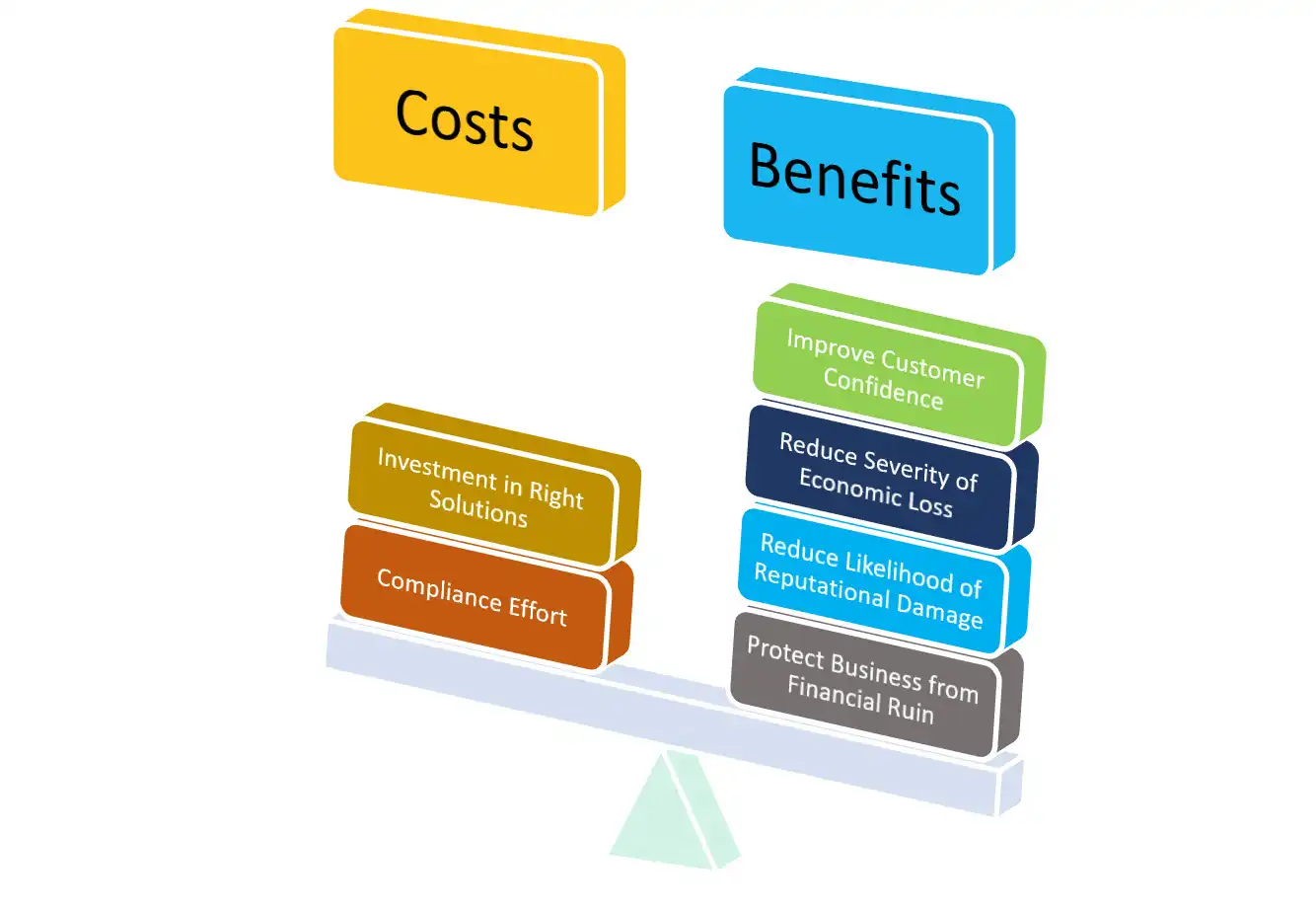
For small businesses, complying with the laws could help protect you from being financially ruined by a cyberattack. Studies reveal alarming facts about attacks and consequences on small businesses when security measures are inadequate:

What security measures and actions can small businesses take immediately not only to safeguard against cybercrime but also start complying with the federal law? Well, there are several of what we call Common Sense IT Security Measures that you, your team or consultants can start implementing right away. These measures encompass policy, procedures, training, automation tools and risk mitigation techniques.

For those who are concerned about being compliant with the law, it is worth keeping in mind that security requirements haven‘t changed that much in a decade. As an agency representative said earlier in the year, “the biggest change (in requirements) lies in the need for contractors to a) demonstrate compliance and b) self-report security deficiencies to the authorized DoD CIO” in a timely manner as specified by the law. Recognize two other differences; a) there is a rapid and aggressive rise of cybercrimes and b) scrutiny for suppliers to adopt proper company IT security measures is heightened by both federal agencies as well as end-user and business customers.
As investors, senior management and owners of small businesses, you do want to act and act quickly to both protect your business and investment, as well as comply with the law. If you have not started evaluating your IT security risks or identified the gaps between your existing security environment and the requirements of the law, you need to start immediately. If you do have a good understanding of your gaps but haven‘t remediated those gaps, you probably want to start developing an action and remediation plan quickly. Rest assured the Agency you do business with will be enforcing these cybersecurity laws because if they didn‘t our nation‘s systems and sensitive data could be put in danger.
In a nutshell, some of the best security measures are those that are basic, practical and common–sense. Small and larger businesses are reminded to take these precautions. Before you rush into creating complex security programs or purchasing expensive security technologies, you should first ensure you understand where your biggest risks lie, prioritize remediation needs to protect your business and comply with NIST SP 800–171 requirements. When addressing gaps, ensure the basics, highest risk areas, low-hanging fruit opportunities and those remediation issues that take a long time to resolve are tackled first. You may be surprised to find that many of those gaps can be easily addressed by implementing common sense IT security measures discussed in this article.
Last but not least, if you don‘t have internal IT security expertise, seek professional or consulting assistance from the experts. Don‘t throw good money away on bad decisions or buy security products you don‘t need or do little to help you defend your systems or comply with the law. There is no silver bullet that will allow companies to comply with NIST SP 800–171 requirements or address all your IT security needs. No one product is designed to address the range of cyber security threats. Anyone who promises you their product will do so is a fraud. Google ‘cybersecurity products’ and you will find no less than 22 million search results. An expert can help you narrow down the list to a handful of products that work best for your needs and environment. Also bear in mind that a reasonable solution should encompass training for your people, adequate policies, procedures, and processes, and configuration of the right mix of tools to protect your network, data, systems, devices, users and customers. Real-time monitoring, reporting and analytics are also necessary to ensure anything that is broken can be quickly identified, reported, assessed and fixed in a timely manner.
Contact Us Please contact Hararei for an in-depth discussion on using any of our Cloud or Cybersecurity products or services