


With increased snooping on networks, insecure default hardware configurations and an uncertain chain of custody for international networks, what can an enterprise do to ensure their private data stays private? At Hararei, we recommend a secure overlay network that provides secure end–to–end encryption overlaid on the wide area network (WAN). This approach is more secure than trying to retrofit security to the underlying network, and can give increased performance and better resiliency as well.
MPLS, one of the most popular WAN protocols, is not secure as it does not provide isolation from telecom snooping. A breached or untrusted telecom provider can inspect all data transiting the network. This may be fine if you‘re operating in some highly regulated environments, however there are many where it is not acceptable. Private leased lines provide the best protection, however are still prone to snooping and default open hardware configurations. International private leased lines are very expensive.
IPSec, a popular open source approach to providing encrypted tunnels over the Internet is not scalable as the operational overhead of managing all the links takes expert level and knowledgeable technical resources at scale. Any more than a handful of IPSec tunnels will overwhelm technical staff with configuration complexity. The best reason not to use IPSec is that single misconfiguration may expose that traffic.
Many network routers are deployed with default credentials, although this is improving in recent years due to publicity attached to this popular attack vector. Many though, still have default credentials in production. Any one of these compromised units are able to be used as an attack vector.
Adding a secure overlay network allows an enterprise to bypass these risks, as the network traffic is encrypted before it reaches the first WAN router, and decrypted only by the intended devices in the remote location. Snoopers only see encrypted traffic. Compromised routers also only see encrypted traffic. The data is encrypted before it leaves the customer data processing facility (private data center or public cloud) and cannot be read by intermediary network devices.
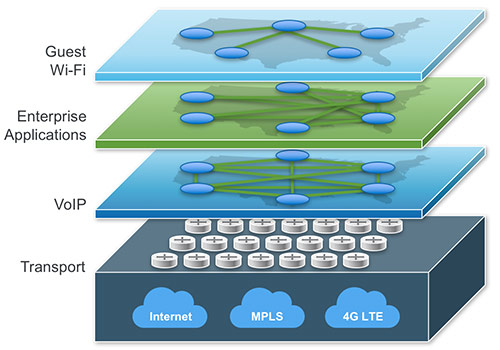
Secure overlay networks may be created for different functions, with different network characteristics. That traffic can be isolated into a separate overlay network
In large complex enterprises, there may also be a need to segment secure traffic, disallowing communication between business units. One operational unit may require WAN separation from another unit. By creating separate overlay networks for each business unit, the underlying WAN can be shared allowing economies of scale for the whole enterprise while still providing the required separation. If this approach were not followed, dual provisioning of WAN links would have been required.
Hararei can help you implement a secure virtual overlay network. Whether the requirement is a single encrypted network link, a secure private branch network, or secure connectivity to public cloud Hararei can design and implement a solution.
Hararei are channel partners for Silver Peak, with their Unity Edge Connect® products, and have experience with secure networking. Contact Hararei for a free briefing and demonstration of the Silver Peak SDWAN solution for implementing a secure network overlay infrastructure.
We are a Cloud generation solutions provider committed to helping clients prepare for, adopt and deploy the latest generation of applications and IT infrastructure in agile environments.
Let Hararei help you implement secure networking. Contact us for a no obligation consultation, or to arrange a no cost trial.
Visit us on the Internet at www.hararei.com